Top Security Risks of Cloud Computing, how does it work?
Cloud Data Security For Business is a critical interplay of cloud security controls, cloud security technologies, procedures, and rules. Ideally, a professional cloud security company must manage and monitor a cloud security strategy.
Access and Identity Management
To manage access to data, businesses must have an “Identity and Access Management (IAM)” system. It is possible that your Cloud Data Security For Business company may interface directly with your existing IAM. Otherwise, cloud providers offer their own in-built IAM with an offered cloud security solution. A good IAM has the ability to limit who has access to your cloud apps and data. Cloud apps security tells what they can do to your data and apps, and what data and apps they can access.
Cloud Security Monitoring and Prevention
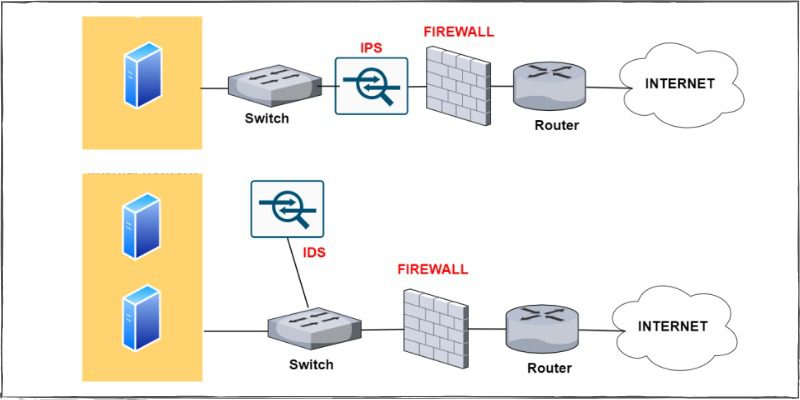
The cornerstone of cloud security monitoring comprises intrusion prevention systems (IPS) and intrusion detection systems (IDS. IDS and IPS technologies help to detect existing and prospective threats. They assist in cloud endpoint security against businesses ‘ cloud security policy. The IPS tools incorporate cloud security features to protect against an intrusion and notify you to watch for it.
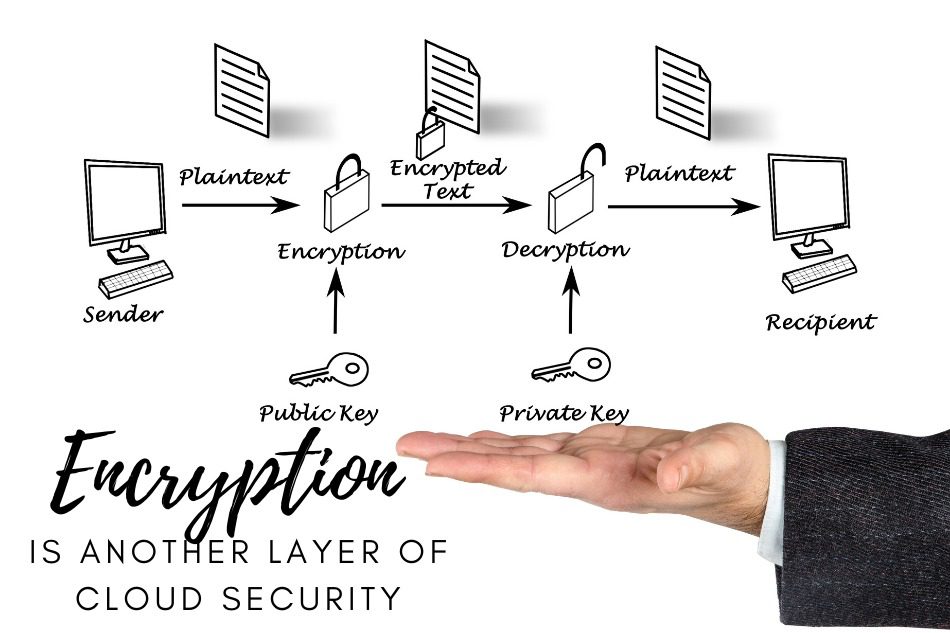
Encryption
You’re transmitting and receiving data from a cloud application platform, which typically stores it in encrypted infrastructure. It also implies that without a password that only you have authority to, decoding the data will be almost difficult without your assistance.
Security Risks of Cloud Computing or Cloud Data Security For Business tools and techniques
No matter where you run your corporation, cloud security concerns are critical everywhere. You’ll be vulnerable to denial of service attacks, SQL injection, malware, data loss, and data breaches. Considering these risks, high cloud storage security is needed. All of this may have a major effect on your business brand and end result.
Why Do We Need Cloud Security?
As Cloud Data Security For Business technology becomes more widely used, the demand for cloud security is growing. This need is increasing in conjunction with the quantity and variety of cyber threats, which are both growing all the time. In light of the cloud security concerns associated with cloud adoption described above, failing to mitigate them may have serious consequences.
Cyber Security Cloud Threats are Continuously Increasing
The growing skill and number of cybercriminals is a driving factor for using safe private cloud security best practices. As a way of putting a number on this threat, we would refer to the (ISC)2 Cloud Security Report. The report says that, in 2019, 28 percent of companies suffered a cloud security incident. According to the UK government cloud security agency, 32% of UK companies have had their systems hacked in the last year.
Preventing Data Loss and Data Breaches
The accelerated number and amount of data loss and data breaches is a result of increasing cybersecurity threats. According to Norton’s Emerging Threat Report, over 4 billion data were stolen during the first half of 2019.

Maintaining Business Continuity
Good cloud security tips are essential for ensuring the continuation of your business operations. Proper cloud network security makes your network or cloud safe from attacks such as a denial-of-service (DDoS) attack. Unplanned failures and system downtimes stop your sustainability and affect your financial performance. A study by Gartner estimated the average cost of this downtime to be US$5600 per min.
Avoid Compliance Violations
Cloud security involves the danger of compliance breaches, we should know that. To illustrate the consequences of non-compliance, look no further than Germany’s federal privacy regulator. They have recently fined 1&1 Telecommunications €9.55 million for breaching the EU’s General Data Protection Regulation (GDPR). Thus it is always recommended to consult professional cloud security companies to avoid the probability of such high compliance violation fines.
5 cloud application security best practices
If you are just getting started with how to best protect your business’s cloud data and enhance your cloud data security, keep reading. As a matter of fact, there are five simple cloud data security best practices, discussed in this cloud security blog, that will help you keep your organization protected from external threats and nation-state attacks.
In fact, only security practices that are implemented will help protect you against potential attacks. Offering cloud security training to any business’s employees and implementing these cloud computing security best practices would assist to minimize the damage caused by a cloud security attack.

Enable Two-Factor Authentication
Make sure your employees have installed a two-factor Authentication method in the system. Two-factor authentication is becoming a standard part of web and mobile security. It uses to ensure that only authorized users have access to an account and/or data. It consists of a code and a password that will send separately via cell phone or text message to a service provider’s phone. When a hacker or service provider tries to access information from your account with either method, the service provider will receive a message. This message contains the requested information but without your actual password. So, they cannot do without the secure code, which is different from your password. This makes it much harder for them to get around the 2FA security.
Encrypt data at rest and in transit
The cloud is a big deal for business. Cloud security is vital to protecting your business and customer data. As the benefit of managing data in the cloud increases, so does the responsibility to protect data locally by implementing appropriate data security practices. Modern technology enables businesses to quickly respond to changes in demand. Businesses respond by serving clients with customized information and material, reducing human error, and improving the service quality. The issue is most vulnerable when data is being exchanged among disconnected applications. Also, changing without proper review is responsible for high chances of attack. In this case, data is not end-to-end encrypted. So encryption keys are used to protect sensitive data in cloud storage systems. This encryption protects it from unauthorized access either at transit or at rest.
Conduct Cloud Security Testing Regularly
As a business owner, you are responsible for keeping data safe and private. The data in your cloud environment can be anything from customer database information to intellectual property. It’s your responsibility to protect it. Even though there is a greater risk in this type of environment, many companies are not recognizing the importance of implementing a recovery plan in place before it is too late. To prevent data loss or damage to sensitive data in your cloud infrastructure, make sure you regularly conduct security tests to ensure that all potential risks have been mitigated.
Consider off-site data backups and alternatives
Cloud security is a hot topic. There are many tools that can help improve the security of your cloud environment, but it’s always possible that an attack can take place through malicious software like viruses or trojans. Protect what you’ve already stored by making sure to do backups, and always make sure that said backups are stored elsewhere from your main data for this very reason.
Be proactive with security, not reactive
Someone has your email address, they can contact you at any time and even threaten to publish your private information if you don’t do as they say. Although, proactive steps you can take to protect yourself include; – Creating a secure business email address. – Use a unique password for each account you have. Therefore, make sure your online banking information is stored in a separate place from your other personal information. Unfortunately, most companies treat security at the time of the attack.
To summarize
Cloud security breaches can occur when you least expect them, so it’s important to put your plan into place now to make sure your business has considerable protection. Moreover, moving to a cloud environment requires a comprehensive approach from day one to ensure security. Furthermore, with many variables, make sure you’re working with the right partner to achieve your results.









