What is a cloud security mechanism?
4 Cloud Security Pillars mean protecting your sensitive information from unauthorized users and hackers through encryption and password protection. In fact, Cloud Security is the digital form of locks, keys, and safes which has been around for hundreds of years. The basic concept is that you keep your data on a remote server that you can access anywhere in the world. Moreover, this dramatically reduces the need to carry files around on a USB hard drive or email them back and forth.
Why is it important to have a strategy for Cloud Security Pillars?
Tolerance for breaches and data theft has never been so low. However, when we think about security, the first thing that comes to mind is that we want to protect our data and make it safe from malicious attacks. The first step for a cloud security strategy is to determine the needs of your company and align those with the capabilities of the cloud providers. One needs to assess what their clients’ concerns are in terms of data security and compliance along with their own level of expertise to identify a partner that can meet their needs.
What are the components of Cloud Security Pillars?
Communication networks, servers, and data storage comprise the bulk of the cloud infrastructure. Cost savings may also be achieved by the use of a hardware abstraction layer in the cloud architecture, which permits the virtualization of resources.
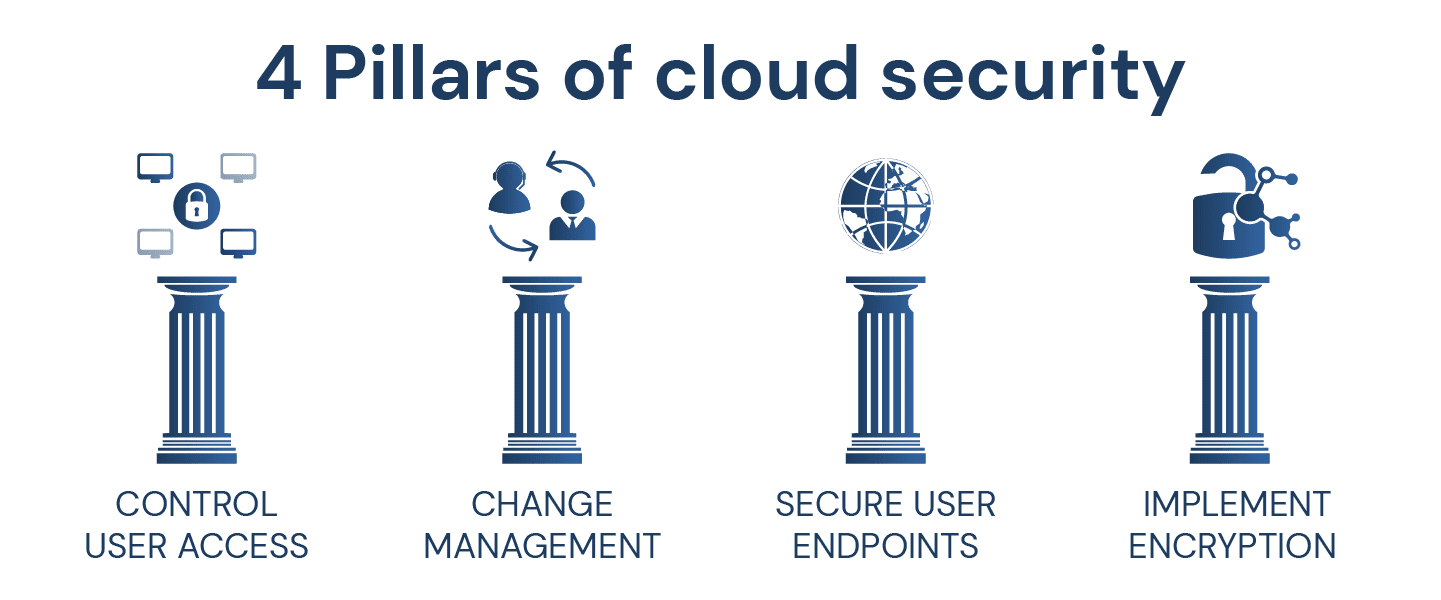
The 4 Pillars Cloud Security strategy or cloud security mechanism
To protect your company’s sensitive information and resources, you need a cloud security strategy. As the cloud continues to evolve and take over the business world, it’s important for IT professionals to understand what cloud security is, why it’s important and how to implement it. Here are four of the most important pillars of a cloud security strategy and features of a mobile cloud.
1. Control user access
In order to control user access to the cloud, a business must design its security strategy. This strategy is essential for data protection. However, a company must develop a plan which includes proper security solutions, training and education of employees, and a process for updating cyber-security as time goes on. The following are some considerations when creating a security policy:
Identify your cloud provider
Review their security practices in detail to ensure that they meet your requirements before moving any data there.
Understand the different security risks of using the cloud
Consider all potential threats to your data in transit, such as hacking and phishing scams, as well as data loss during service disruption or termination of the contract with the provider.
Legal agreements
Ensure that your network meets all service level agreements (SLA) for both upload and downloads speeds, particularly if you are transferring large amounts of data to the cloud or running processes that require significant bandwidth or low latency connections like VoIP calls or online gaming sessions.
2. Change Management
In a cloud computing environment, the management of security is more dynamic. Because, changes to the infrastructure can be made quickly. Security teams must have the ability to make changes to the cloud infrastructure as is needed. This requires additional policy management, which requires careful considerations for both scalability and performance.
Change center
A stakeholder-driven, collaborative process for managing, controlling, and communicating changes.
Change categorization
A structured approach that identifies the impact of changes and provides direction on who will approve and review them.
3. Secure your user endpoints
Businesses are turning to the cloud for its flexibility, scalability, and cost benefits. But a cloud-based architecture is also inherently less secure than a traditional, in-house IT deployment — which means it’s all the more critical to ensure your users’ endpoints are protected.
With the right security strategy and tools, organizations can maintain control of their data while still leveraging the many benefits of a cloud-based approach.
4. Implement encryption
If you’re looking to store files in the cloud, encryption is one of the most important things you can do. Cloud storage services like Dropbox and Google Drive encrypt the data they store on their servers. Ensuring your files remain encrypted at all times is a good strategy for preventing unauthorized access. Encrypting your files before uploading them ensures that even if an attacker gains access to the server, he or she won’t be able to view the contents of your files.
Symmetric encryption:
This type of encryption uses one key — both parties in a conversation use the same one. Symmetric keys are very difficult to crack since there’s no way to get around needing both parties’ keys to decrypt data.
Asymmetric encryption:
This type of encryption uses two keys. One is the public key, which is distributed widely to anyone who wants it. The other is the private key, which is kept secret. Any message encrypted with one key will only be readable with the other one.
How can we effectively implement a cloud security strategy?
There are three steps to a successful cloud security plan or Cloud Security compliance Strategies
- Add additional layers of protection. Provide private connection instead of using the public internet to access an internet cloud service.
- Data security.
- Keep your cloud service provider on their toes.









